Handling configurations in app development, especially with Kubernetes, can quickly turn into a real headache. It's more than just tracking various settings across different setups; it's crucial to maintain consistency, security, and efficiency in these configurations. This is where Azure App Configuration comes into play. It's built to cut through the complexity of traditional configuration management, offering a centralized solution that's both scalable and secure. With Azure App Configuration, you can forget the hassle of manual updates and redeployments. It's all about making configuration management as smooth and straightforward as possible, giving teams the tools to keep things streamlined and under control.
This version aims to convey the essential message without the fluff, focusing on the practical benefits and the problem-solving nature of Azure App Configuration for developers working in cloud-native environments.
Why Azure App Configuration?
Azure App Configuration stands out because it addresses common challenges head-on. Traditional methods like embedding settings in code or using environment variables are more than just cumbersome; they lack the agility and security modern applications demand. Azure App Configuration provides a single source of truth for your application settings and feature flags, supporting dynamic changes and simplifying the management of cross-environment configurations. With capabilities like feature management, it becomes trivial to implement A/B testing or gradually roll out new features, directly impacting the application's agility and user experience.
Setting Up Azure App Configuration
Setting up Azure App Configuration is straightforward. You create an App Configuration store through the Azure portal and begin adding your configuration keys and feature flags. The real magic is in organizing these configurations, using labels to differentiate between environments or application versions, and ensuring the correct settings are applied at the right time. This setup enhances security by segregating sensitive settings and promotes operational efficiency by centralizing configuration management.
While the App Configuration is being created, let's continue on.
Integrating with Kubernetes
Integrating Azure App Configuration with Kubernetes brings the best of both worlds: Kubernetes' powerful orchestration capabilities with Azure's robust configuration management. The integration process involves setting up Azure Managed Identity for secure access, configuring the Kubernetes cluster to recognize and use this identity, and then seamlessly accessing the configuration data from your applications running within the cluster.
Make sure you're logged into the cluster and run the following command to install the App Configuration Provider
helm install azureappconfiguration.kubernetesprovider oci://mcr.microsoft.com/azure-app-configuration/helmchart/kubernetes-provider --namespace azappconfig-system --create-namespaceNow, it's time to create and configure the identity that will be used to pull the configurations from the resource. If your cluster doesn't have Workload Identity enabled, then I suggest stopping here and reading this post I wrote about the subject https://florinloghiade.ro/azure-workload-identity-in-aks/
If you have WI enabled, then continue on.
The below snippet requires filling in the information, and it will configure a managed identity in the cluster resource group with the OIDC information of the cluster.
$RESOURCE_GROUP = "<RG>"
$CLUSTER_NAME = "<CLUSTER_NAME>"
$LOCATION = "<REGION>"
$SUBSCRIPTION = "<SUBSCRIPTION_GUID>"
$USER_ASSIGNED_IDENTITY_NAME = "<MI_NAME"
$FEDERATED_IDENTITY_CREDENTIAL_NAME = "<A NAME FOR THE IDENTITY>"
$AKS_OIDC_ISSUER="$(az aks show -n $CLUSTER_NAME -g $RESOURCE_GROUP --query "oidcIssuerProfile.issuerUrl" -o tsv)"
az identity create --name "$USER_ASSIGNED_IDENTITY_NAME" --resource-group "$RESOURCE_GROUP" --location "$LOCATION" --subscription "$SUBSCRIPTION"
az identity federated-credential create --name "$FEDERATED_IDENTITY_CREDENTIAL_NAME" --identity-name "$USER_ASSIGNED_IDENTITY_NAME" --resource-group "$RESOURCE_GROUP" --issuer "$AKS_OIDC_ISSUER" --subject system:serviceaccount:azappconfig-system:az-appconfig-k8s-provider --audience api://AzureADTokenExchangeBy this time, the App Configuration resource should be deployed, so now it's time to assign the newly created managed identity data reader RBAC and afterwards to pull the endpoint details to update the yaml file
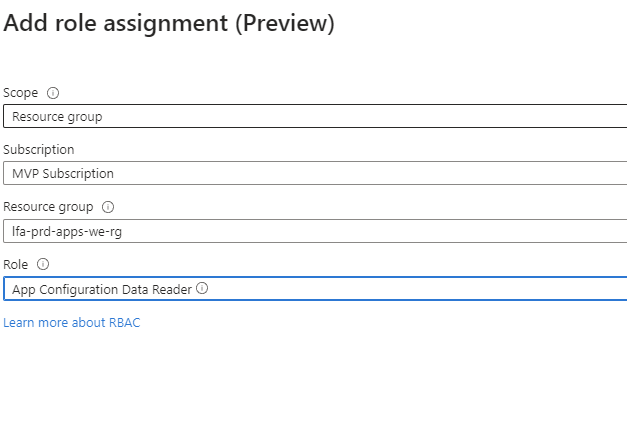
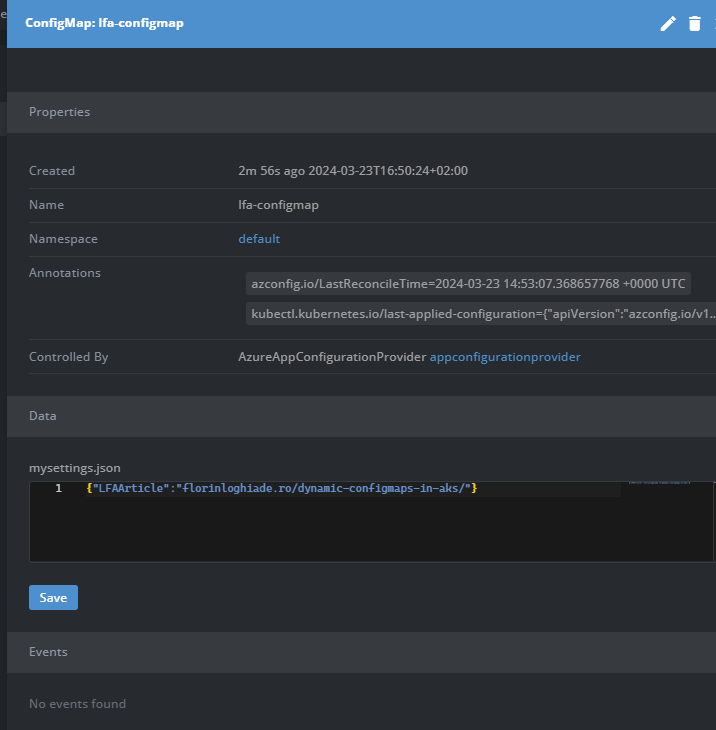
While we're here as well, create a Key Value pair so that it pops up in the config map inside the cluster when it's configured.
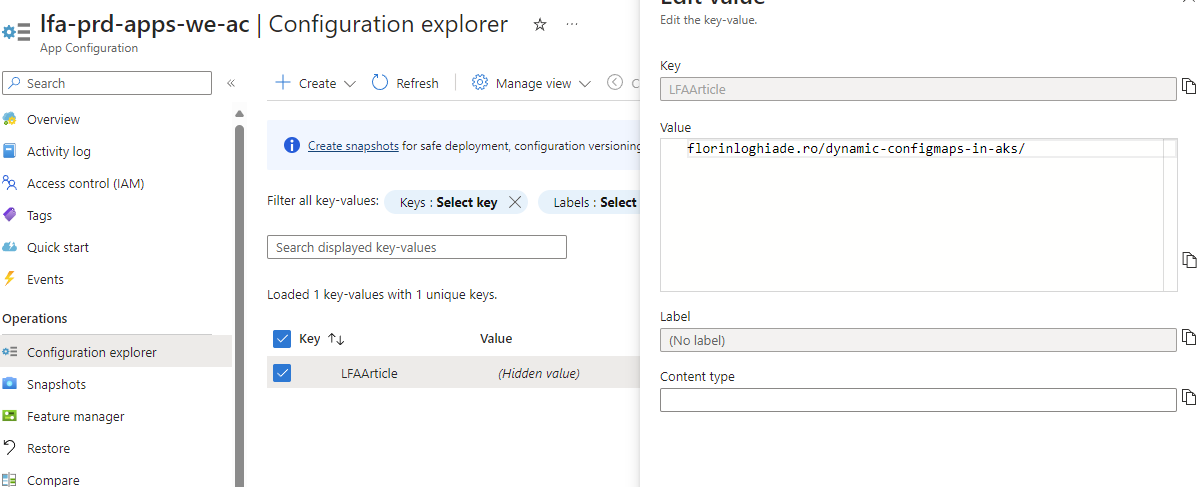
Getting closer to the end; Fill in the yaml file with the necessary details and apply it in the cluster.
apiVersion: azconfig.io/v1
kind: AzureAppConfigurationProvider
metadata:
name: appconfigurationprovider
spec:
endpoint: https://lfa-prd-apps-we-ac.azconfig.io
target:
configMapName: lfa-configmap
configMapData:
type: json
key: mysettings.json
auth:
workloadIdentity:
managedIdentityClientId: <MI CLIENT ID>Voila!
TLDR:
Managing configurations can be a pain in app development, particularly with Kubernetes. It's all about keeping settings straight across different environments and ensuring everything is consistently applied, secure, and efficient.
Adopting Azure App Configuration with Kubernetes simplifies configuration management and introduces good practices that can significantly improve efficiency. Keeping sensitive configurations secure, dynamically updating settings, and structuring configuration keys are just the tip of the iceberg. Implementing these practices ensures that your Kubernetes deployments are not just robust and scalable but also maintainable and cost-effective in the long run. And if you're keeping configurations in Key Vault, STOP IT.
That being said, have a good one!








