Azure Security Center - Scan your container images for vulnerabilities
Do you deploy your apps in containers? Do you scan them for security vulnerabilities? No? You should. Containers are all the rave this year an
Containers are all the rave this year and will continue in the following years; The problem that we’re going to face really soon (honeymoon effect) with the boom of containers is that security is still important even here.
Compared to a regular VM, yes containers are much more secure because they have a lower footprint but that doesn’t mean you shouldn’t care about security. You can hack a container as simple as a simple VM. You’re running Apache, NGINX, Node? If you’re running old versions that have vulnerabilities, guess what, they can be exploited ?
In Azure we never had a native capability of scanning container images for vulnerabilities, we had to rely on two vendors with their solutions and to integrate our pipelines with them. The problem you can imagine is that you have to buy a license for a new solution, integrate it and maintain it. Some companies already did that but others relied on that Azure Container Registry does that out of the box. Spoiler alert: it doesn’t.
The need to install third-party solutions is over (somewhat) because Azure Security Center got integrated with Qualys container image scanning and we can get a native experience with direct billing from Microsoft. Win-Win I say ?
First of all, you need to run Azure Security Center on the Standard Pricing model. Second, you need to check that you want Azure Security Center to scan your container registries:
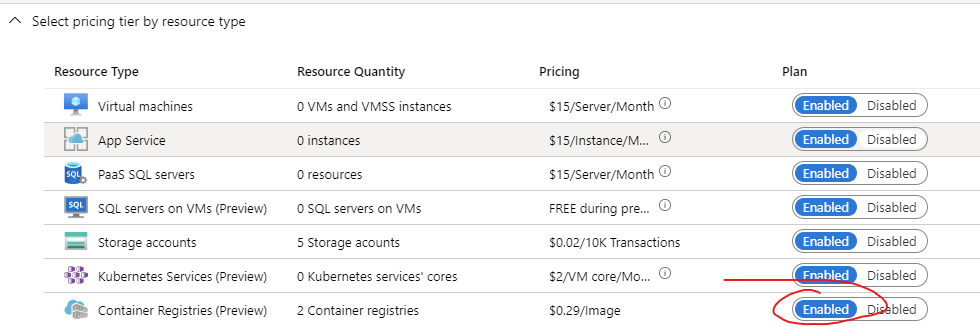
Second, you need to have Docker Desktop and AZ CLI installed :
I want to open a parenthesis here: My development/operations environment runs on a VM under Hyper-V. I keep everything in that VM so that my main operating system remains in a very pristine state (mostly pristine, I do game a lot). Anything related to work is kept in a VM and if something goes wrong, I revert the checkpoint and not the entire OS.
You’re welcome.
Let’s continue.
After that you run az login and then az acr login –name <youracrname> and run the following docker commands:
docker pull vulnerables/web-dvwa docker image list docker tag vulnerables/web-dvwa:latest <youracr>.azurecr.io/vulnerables/web-dvwa:latest docker push <youracr>.azurecr.io/vulnerables/web-dvwa:latest
I usually prefer the use of Portainer ( https://www.portainer.io/ ) for these types of operations because it’s much more simple to have a visual representation of everything configured on the host machine and do the much testing without much back & forth.

After the push, the image will be available in the Azure Container Registry and Azure Security Center will automatically pull the image and start scanning it for Vulnerabilities. This process typically takes 15 to 20 minutes.
Flow: From Push to ASR
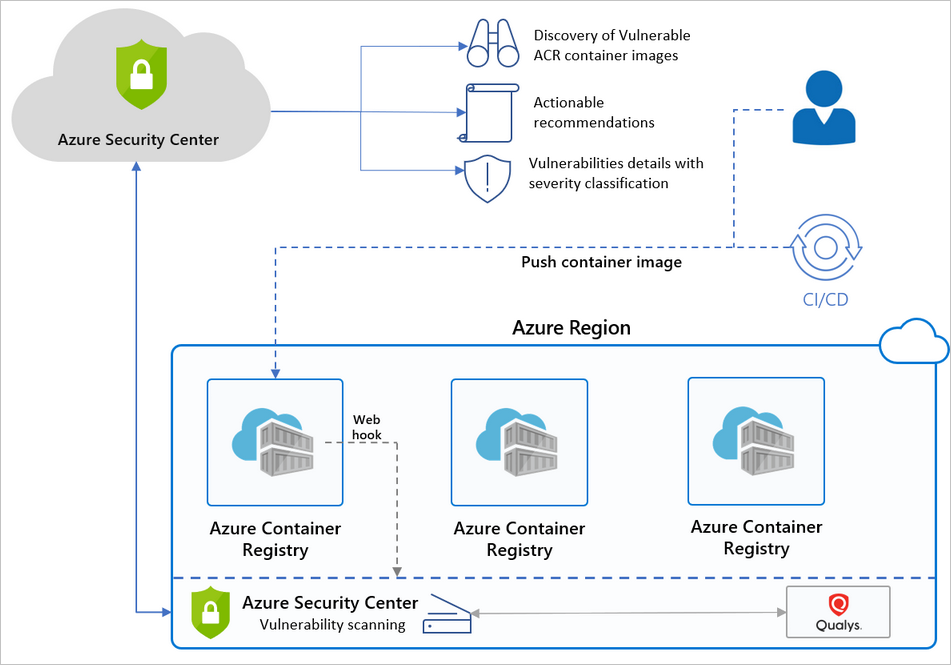
Once Azure Security Center receives the scan output from Qualys, you will be presented a list of recommendations under the container tab in the recommendations tab.

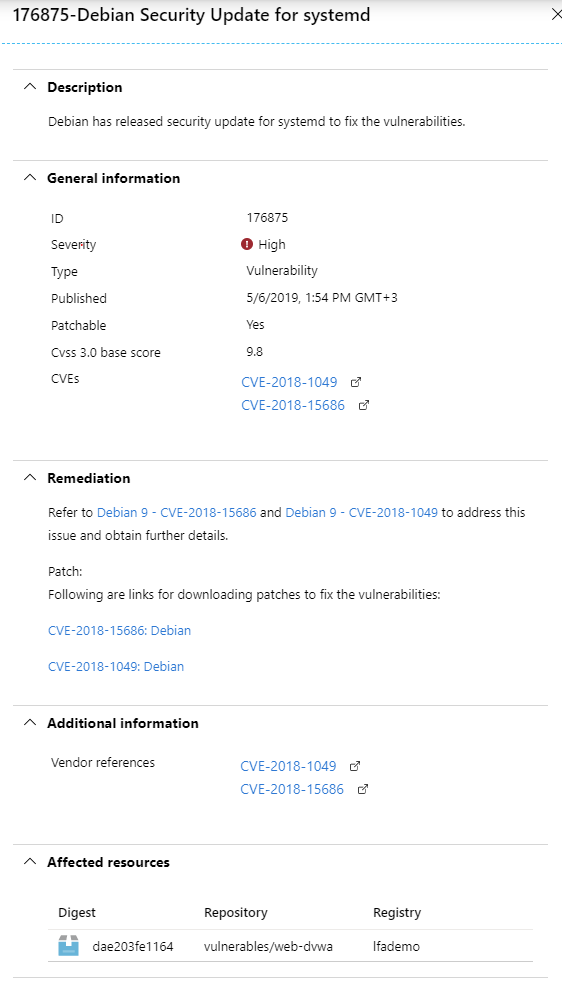
By clicking on the repository which has a recommendation list, we see the security checks that have been done with Qualys with a security criticality matrix based on low-medium-high depending on the CVE and if a patch is available.

If we drill down in the list, we will see more information about the security risk of the image:
To be honest, this offering looks great in the context of container security because the alternatives we had in the past was to buy a license from Aqua or Twistlock and have a VM do all the scanning.
I played around with Aqua in the past and I can say that the current offering in Azure Security Center isn’t there yet but we’re talking about a preview offering after all ?
In the end, I prefer the use of a system integrated into Azure rather than adding 3rd parties in the mix. From my point of view, this is a winner and I will be integrating it as much as possible.
That being said, have a good one!
