Azure DevOps - Workload Identity Federation
In a previous blog post, I discussed Workload Identity Federation in AKS, the successor to the Azure Pod Identity solutions and a more elegant
There’s no shortage of solutions when it comes to NGFW in the cloud but they all come at a hefty price, steep learning curve and require continuous maintenance from the ops teams. We have solutions from Barracuda, Fortigate, Checkpoint, Cisco and so on but in the end, they are some Linux Virtual Machines that have some third party software on them with or without built-in HA. Azure Firewall is here to provide another solution that can solve some of these issues that come from NVAs deployed in the cloud…but not all of them.
Let’s start off with what Azure Firewall can do and what it can not do at this moment:
If you compare Azure Firewall with any NGFW solution from the marketplace you will see that it lacks a lot of features and might not appear to solve any of today’s current issues but stay a while and listen ?
Think of this. The current third-party firewalls started from the on-premises environment as physical appliances and then got slowly evolved towards virtual appliances, so most (not all) of them have features that are useless in the cloud (and you pay for them). Another thing is that you have to manage them end to end and even back them up. They are not a managed service that you licenses from a provider and just consume the service, it’s a full-blown IaaS machine and the list can go on.
Azure Firewall is a cloud-native stateful firewalling service that is not deployed as a VM. It’s a fully managed security service by Microsoft that scales automatically and requires no maintenance from the user (hence the fully managed part), and the only thing that you need to do is to configure it correctly.
At the time of writing this post, Azure Firewall blocks all inbound/outbound traffic with the possibility allow IP addresses, FQDNs or CIDR blocks and it deploys a UDR in the VNET it creates to redirect the 0/0 traffic through it, just like an NVA and it also plugs into Azure Monitor and I suspect that it will plug into Traffic Analytics and ASC because it makes sense on the long term.
Deploying an Azure Firewall is pretty simple and it doesn’t require too much configuration and a reference architecture looks something like this:
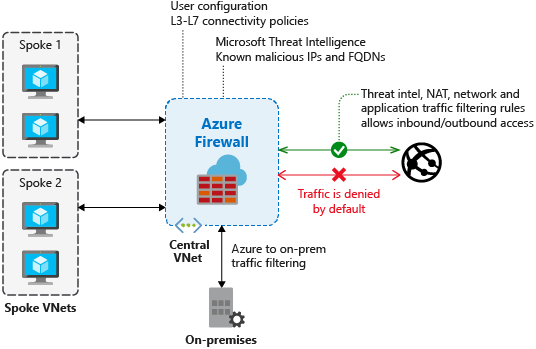
The best-practices around Azure Firewall show that it should be configured in a hub & spoke architecture where you deploy your core / shared services and have spokes that connect through them. The main reason for this is that the entry price is 780 EUR per scaling unit. The way I see it is that in combination with NSGs, App Gateway WAF and other services like DDOS Protection Standard would add more value to the enterprise client than anything else.

Finally I would like to add that from my point of view, Azure Firewall is still a work in progress but a very welcome addition to the cloud security offering that Microsoft adds in Azure.
